There has been a lot of talk about ad blocking in regards to how certain ad formats are annoying internet users, but not nearly enough about the threat Malvertising and leaving it unchecked is causing to internet users, businesses and the society. The Internet finds itself in a malware epidemic, one that is fueled by the biggest ad networks and publishers. More than any other single thing, the epidemic can be made worse by attempts to stop internet users from blocking ads.
In a recent article by Wired [1], malvertising, the practice of delivering malware to a user’s device through an ad, is described as “hacking us softly”.
This disction between the old way of malware delivery where a user could effectively reduce chances of exposure by using common security software and avoiding clicking suspicious links, and when malware is delivered through an ad, is that there is very little the user can do to avoid exposure using any traditional security solution or behaviour based practice.
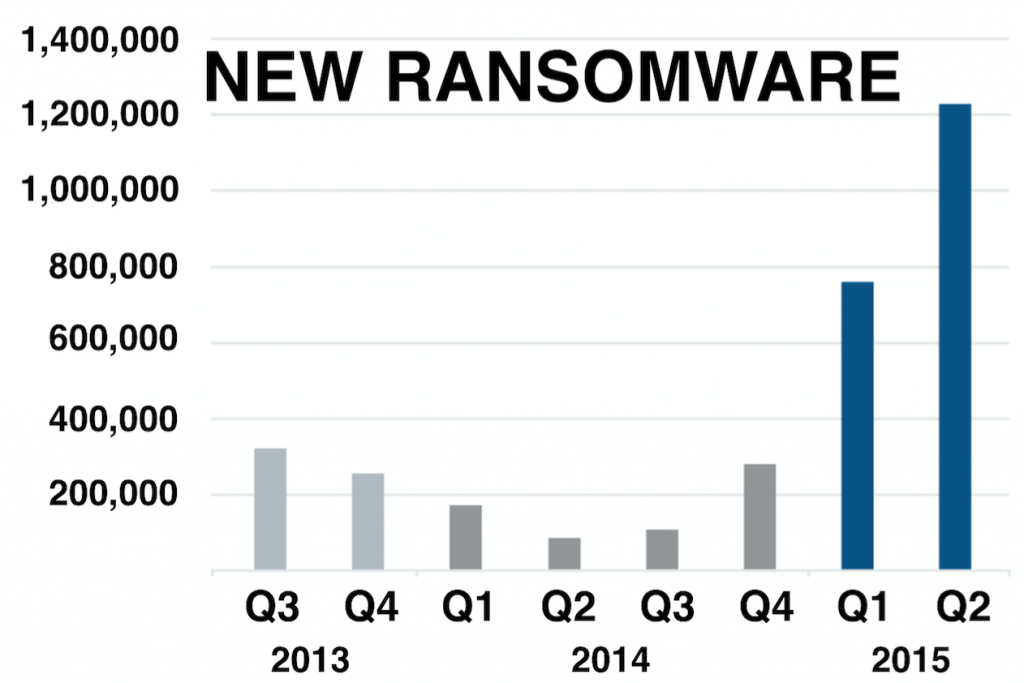
What is making the threat even more worrysome for internet users, is where these Malvertising attacks are being carried out. For example last week BBC reported that their own site, together with 13 other major sites were being used by criminals to deliver Ransomware on to users’ devices[2].
Examples of major sites recently used in Malvertising attacks to deliver Ransomware on to users’ devices include:
- MSN
- BBC
- The New York Times
- AOL
- Newsweek
In the last quarter of 2015, Ransomware attacks increased by 26% quarter-on-quarter [3] and the word ‘epidemic’ have been widely used in the media and by security experts[4] to describe the dramatic growth in Ransomware activity.
Another recent report found that Google’s Doubleclick ad platform was used for targeting specific countries with Malvertising attacks[5]. Because malvertising attacks have been and continue to be connected with ad fraud malware [6] and ransomware, an enemy of state can effectively use malvertising attacks to directly cause harm to a given nation state and its people.
In the US there are many reports from police stations where they have to pay for unlocking the data in their systems after being hit by Ransomware[7]. This is not a surprise as Google Doubleclick and other common ad platforms allow targeting of ads based on IP address and even company name. This way public officials and key state-level services and infrastructure could be easily attacked using the same methods covered in the sources referenced in this article.
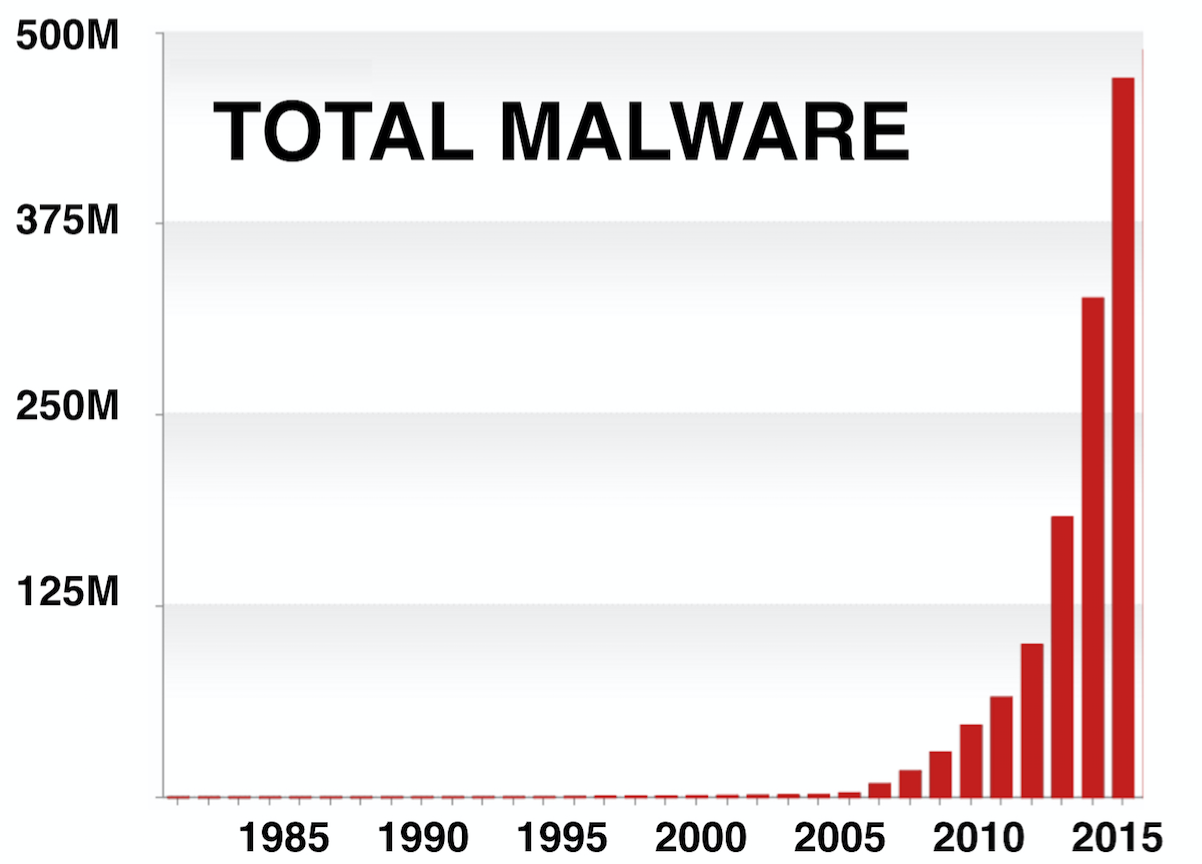
It is not just Ransomware that is growing dramatically, but there is an even darker picture in overall Malware situation.
With a recent report claiming 325% year-on-year growth for malvertising[8], delivering malware through ads is rapidly becoming the preferred method for targeted and untargeted malware at any scale. Cisco’s Annual Security Report [8], found that ads were the second most common source for malware exposures with 16% of all exposures.
In a Senate Testimony, Online Trust Alliance reported that while in 2013 year-on-year growth for Malvertising attacks was already 200%, there were already at that time over 12 billion malicious ads[9], or more than 4 for every internet user. As the recent reports show, these attacks are increasingly being conducted through trusted major sites.
SOURCES:
[1] http://www.wired.com/insights/2014/11/malvertising-is-cybercriminals-latest-sweet-spot/
[2] http://www.bbc.co.uk/news/technology-35821276
[3] http://www.timeslive.co.za/scitech/2016/03/23/Epidemic-of-ransomware-is-growing-hacking-threat
[4] https://blog.kaspersky.com/ask-expert-ransomware-epidemic/9332/
[7] http://www.darkreading.com/attacks-breaches/police-pay-off-ransomware-operators-again/d/d-id/1319918
[8] http://go.cyphort.com/rs/181-NTN-682/images/Malvertising-Report-15-RP.pdf
[/content_container]