In the light of recent high profile malvertising attacks, the adtech industry is finding itself as a center of attention in respect to the ongoing malware epidemic. In this article, we will cover how in fact it is the industry itself that to some extent is causing malvertising attacks to be possible.
EIGHT MYTHS ABOUT MALVERTISING
MALVERTISING MYTH 1.
MYTH: the adtech industry and namely ad platforms that are used for conducting such attacks, are a victim of malvertising
FACT: not only ad platforms get paid for delivering malvertising, but do to negligence and structural issues are a significant cause for such attacks to be possible in the first place
MALVERTISING MYTH 2.
MYTH: malware enters the ad eco-system because of “hacking” or technological vulnerability of some kind
FACT: malware enters because of structural issues and wide spread negligence in the adtech industry, namely the popularity of allowing 3rd-party javascript in to ad delivery
MALVERTISING MYTH 3.
MYTH: adtech companies are “doing everything they can” to keep malware from entering the internet advertising eco-system
FACT: with few exceptions, adtech companies have changed nothing in order to being more responsible or to address the underlying structural issues
MALVERTISING MYTH 4.
MYTH: there are strict auditing processes that adtech companies adhere to in terms of what can be delivered through their systems
FACT: such auditing processes rarely consider javascript payloads delivered together with the ads, but are merely focused on the ad creative itself
MALVERTISING MYTH 5.
MYTH: bigger publishers are less prone to malvertising attacks than small websites
FACT: malvertising attacks are increasingly focused on major publishers, due to their massive reach together with other possible reasons
MALVERTISING MYTH 6.
MYTH: malvertising is typically delivered through small shady ad networks / exchanges
FACT: malvertising attacks take place through major ad platforms regularly, due to poor policies pertaining 3rd-party tags, and poorly understood redirecting practices
MALVERTISING MYTH 7.
MYTH: malvertising attacks are focused on blindly infecting as many internet users as possible
FACT: malvertising attacks are increasingly focused on attacking specific countries and major publishers in that country
MALVERTISING MYTH 8.
MYTH: for a malvertising attack to be effective, user needs to click the ad or take other action
FACT: malvertising attacks are delivering ransomware and other types of malware unconsciously to users’ device
ADTECH’S ROLE IN MALVERTISING
A quick Google search reveals a substantial number of results highlighting the popularity of allowing 3rd-party tags to be delivered together with ads [1]. Google is one of the few ad platforms that does not allow buyers to freely include 3rd-party javascript codes to be delivered inside ads, unless the payload is provided by one of the 2,000 or so Ad Exchange Certified External Vendors [2]. Regardless of Google’s supposedly more stringent policies making it harder to use its Doubleclick platform for malvertising attacks, it is one of the most common platforms mentioned in association with such attacks [3][4].
While ‘modern’ malvertising incidents have been reported since 2004 [5], Doubleclick was sued for a large scale tech support banner ad scam as the actual perpetrator already in 2003 [6]. An attack that can be considered an early form of malvertising. Since 2004 Doubleclick has been frequently reported for being used in malvertising attacks [7][8][9][10] and most recently in March 2016 [11]. Such is the track record of the largest, best resourced and in terms of related security policy, the most responsible company in the adtech eco-system.
In a Black Hat 2013 live demo [12] by security researchers Jeremiah Grossman and Matt Johnson from a leading web application security firm Whitehat Security, it was for the first time shown just how easy it is to get custom javascript to be delivered together with ads using a common ad network. As a testament to this ease at which malicious payloads can be delivered using ad platforms, one of the inventors of Javascript, Douglas Crockford said “The most reliable, cost-effective method to inject evil code is to buy an ad.” [13]
Because auditing processes in the adtech industry are focused on meeting the IAB Advertising Creative Guidelines [14] and not concerned with the safety of the internet users, there are virtually no obstacles to getting malicious codes to be delivered inside ads using ad platforms in the way they are intended to be used. Because the intended use of the the platforms includes delivery of 3rd-party javascript codes that violate user privacy and function in other malicious ways, there is nothing that stop malware delivery using those same standard functions of common ad platforms. To further complicate things, with only few exceptions such as AppNexus, even larger ad platforms generally tend to have no information security focused staff. This can be easily witnessed through LinkedIn profiles of the employees of such companies.
While malvertising has been an issue for more than a decade, a point illustrating the persistence of the problem on one hand, and the inability of the adtech industry to contain it on the other, the shift towards targeting major sites has brought the topic under wider attention only recently [15][16][17][18][19]. In the light of these facts, it seems fair to argue that IAB’s and its members’ self-regulatory efforts in this matter have failed, and further involvement from outside of the industry is badly needed to address malvertising as the serious threat to internet users, business and civil society it presents[20]. In this respect, perhaps the most alarming trend that can be seen in recent malvertising attacks is the way attacks are targeting specific nations, for example UK [21], Netherlands [22] and Finland [23].
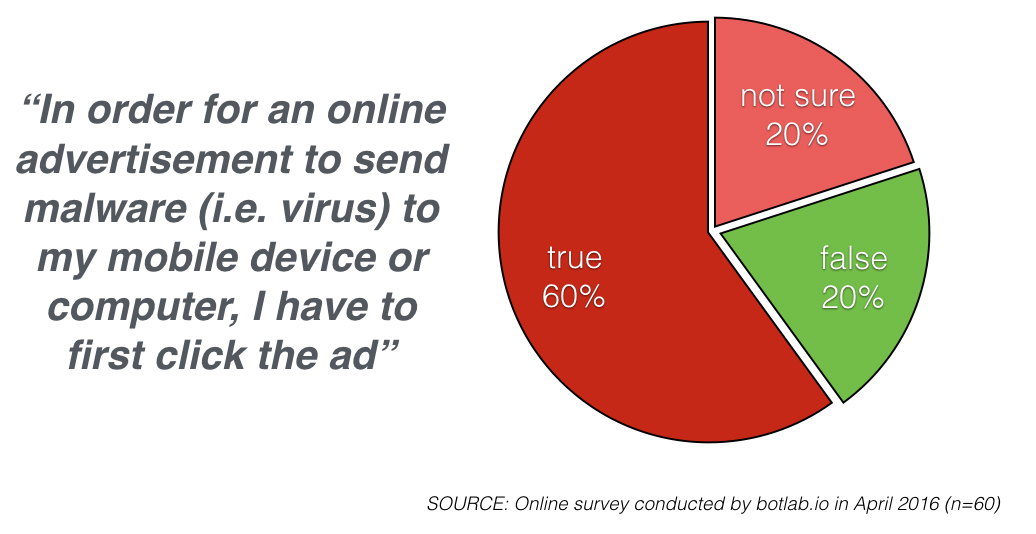
Based on a survey conducted by botlab.io, even savvy users rarely know that malvertising can be used to deliver malware unconsciously to the user’s device. Yet installing of ransoware and malware infecting the user’s device without any action on the users part has become a hallmark of malvertising attacks [24][25][26]
REFERENCES:
[1] https://www.google.com/search?sourceid=chrome-psyapi2&ion=1&espv=2&ie=UTF-8&q=using+custom+javascript+inside+ad+creative&oq=using+custom+javascript+inside+ad+creative&aqs=chrome..69i57.7232j0j7&gws_rd=cr&ei=7wM8V-Bn59fpBKK8jsgP
[2] https://developers.google.com/third-party-ads/adx-vendors
[3] http://www.theverge.com/2014/9/19/6537511/google-ad-network-exposed-millions-of-computers-to-malware
[4] https://blog.malwarebytes.org/threat-analysis/2015/09/large-malvertising-campaign-goes-almost-undetected/
[5] http://news.netcraft.com/archives/2004/08/06/phishing_attacks_using_banner_ads_to_spread_malware.html
[6] http://www.bizjournals.com/pittsburgh/stories/2003/07/21/daily17.html
[7] http://archive.wired.com/techbiz/media/news/2007/11/doubleclick
[8] https://zeltser.com/malvertising-malicious-ad-campaigns/
[9] http://www.cnet.com/news/malware-delivered-by-yahoo-fox-google-ads/
[10] https://www.solutionary.com/resource-center/blog/2010/02/malvertising-and-corporate-security-a-no-win-situation-right-now/
[11] http://www.techtimes.com/articles/141546/20160317/major-ad-based-cyberattack-slaps-top-publishers-with-malware-tied-to-angler-exploit-kit.htm
[12] https://www.youtube.com/watch?v=D6MG2uBIfUI
[13] crockford.com/pp/principles.ppt
[14] http://www.iab.com/guidelines/iab-display-advertising-guidelines/
[15] https://www.trustwave.com/Resources/SpiderLabs-Blog/Angler-Takes-Malvertising-to-New-Heights/
[16] http://www.bbc.com/news/technology-35821276
[17] http://proofpoint.com/us/threat-insight/post/video-malvertising-bringing-new-risks-high-profile-sites#comment-10285
[18] https://blog.malwarebytes.org/malvertising-2/2016/03/top-australian-classifieds-site-serves-malware-in-malvertising-attack
[19] https://blog.fox-it.com/2016/04/11/large-malvertising-campaign-hits-popular-dutch-websites
[20] http://botlab.io/malvertising-a-serious-threat-to-internet-users-business-and-society/
[21] https://blog.malwarebytes.org/threat-analysis/2016/03/a-look-into-malvertising-attacks-targeting-the-uk/
[22] https://nakedsecurity.sophos.com/2016/04/12/massive-malvertising-attack-poisons-288-sites/
[23] http://m.digitoday.fi/tietoturva/2016/03/16/tietokoneesi-on-vaarassa-vaikket-tekisi-mitaan-ilmiossa-havaittu-piikki/20162985/66
[24] http://www.infoworld.com/article/2625124/malware/the-doubleclick-attack-and-the-rise-of-malvertising.html
[25] https://blog.malwarebytes.org/threat-analysis/2015/04/flash-ek-strikes-again-via-googles-doubleclick/
[26] https://blog.malwarebytes.org/threat-analysis/2014/09/googles-doubleclick-ad-network-abused-once-again-in-malvertising-attacks/